$0.00
Get a FREE Cyber Risk Score
Ready for a cyber attack?
Probably Not.
Do you want to have to think of the embarrassment of having to tell your current and former clients and vendors that, because of you, all their private information is now in the hands of hackers. You are now stuck paying exorbitant after-hours emergency fees to your IT provider while your doors to your business are closed for the foreseeable future. Not to mention the potential lost clients, likely lawsuits and fines for violating data-breach/NPI laws in your state. Your bank account on empty, with almost zero bank protection for business accounts.
You don’t have to live like this; Great White Cyber’s Powerful Automated Penetration Test can reset the conversation you have with your team about cybersecurity.
Our powerful automated penetration test will show you how easy it can be for nefarious hackers to get at your information. Don’t worry we will also help you and your team create a plan to make sure your everyone is focused on securing the human element through cybersecurity policies and training
Our powerful automated penetration test will show you how easy it can be for nefarious hackers to get at your information. Don’t worry we will also help you and your team create a plan to make sure your everyone is focused on securing the human element through cybersecurity policies and training
The Great White Cyber Automated Penetration Test is a real-life demonstration of how would be hackers could get into your business, what they could steal or lock down, an easy checkup on user behavior and how IT has been managing things so far —a good test that they’re doing the job you’ve hired them to do.
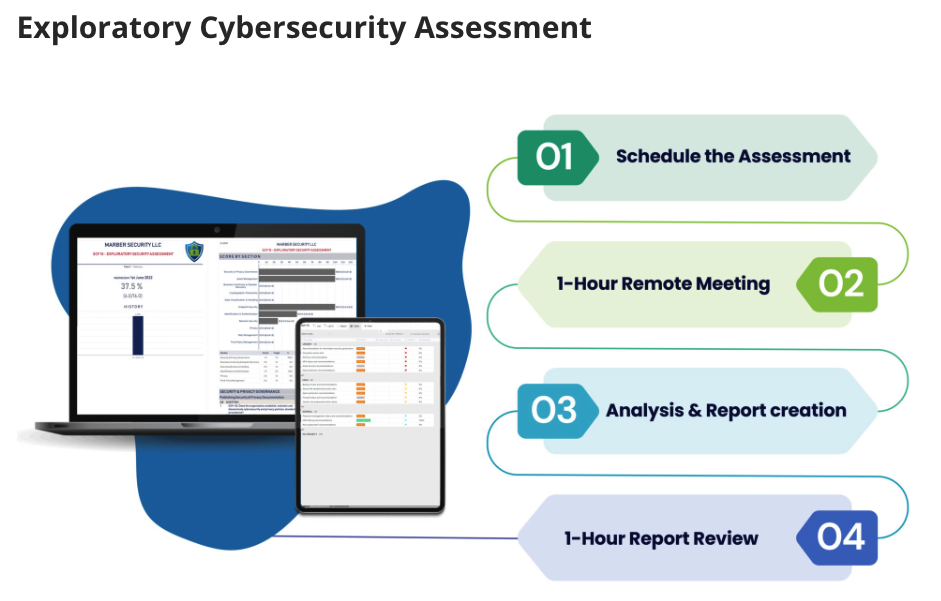
How Great White Cyber’s Automated Penetration Test Works:
- Request your FREE Cyber Risk Score
- 48 Hr test run against your Public Domain
- Analysis & Cyber Risk Score Reviewed
- FREE Cyber Risk Score Report Delivered!
- This FREE Cyber Risk Score report will help you determine if you need to do a full-scale Automated Penetration Test.
Your Thursday is going as planned, coffee in hand, looking out your home office window where you manage your empire and soak it all in. The to-do list is getting knocked out and life is good. Then…the phone rings.
Your account calls from the closing table and wants to know why the money isn’t in the account for the deal everyone is ready to sign? You tell everyone the client said the money was wired yesterday and should be there…but it isn’t and your heart sinks. That feeling in the pit of your stomach starts to churn and just know that something is wrong in a big way.
This happens every single day and most of the time it is from the same source…social engineering via phishing emails that exploit the lack of internal controls in your business and vendor relationships.
Your account calls from the closing table and wants to know why the money isn’t in the account for the deal everyone is ready to sign? You tell everyone the client said the money was wired yesterday and should be there…but it isn’t and your heart sinks. That feeling in the pit of your stomach starts to churn and just know that something is wrong in a big way.
This happens every single day and most of the time it is from the same source…social engineering via phishing emails that exploit the lack of internal controls in your business and vendor relationships.
To keep risks at an acceptable level, policyholders are required to meet basic IT security standards in order to qualify for cyber insurance. At a minimum, a company interested in buying cyber insurance must have the following safety measures in place:
- Employees must receive cybersecurity training and be briefed on security policy.
- All PCs must be equipped with antivirus software and it must be kept up to date.
- Businesses must use central patch management to ensure critical updates are applied in time.
- The company network must be protected using a firewall.
- Business data must be regularly backed up using external media or a secure cloud service.
- Vulnerabiltiies must be identified through vulnerability scanning or penetration tests.
- Companies must use endpoint protection and intrusion detection to stop attacks.
- User accounts and permissions must be actively managed and routinely audited.
- Admin and other privileged accounts must be secured using multi-factor authentication.
Topics covered includes:
- Request your FREE Cyber Risk Score
- 48 Hr test run against your Public Domain
- Analysis & Cyber Risk Score Reviewed
- FREE Cyber Risk Score Report Delivered!
